🏴 Your Crypto Is Not As Safe As You Think


Last Friday, we updated The Ultimate Guide to Airdrops — your one-stop-shop for our team’s predictions on the next dApps to have an airdrop. The first prediction is free for everyone. The rest are available exclusively to ✨ Bankless Citizens✨.
Dear Bankless nation,
Bear markets are a time for self-reflection — so, be a savvy investor and take stock of where your crypto is! What your custody habits are! And how you balance risk and reward!
In today’s issue, we offer a framework for dissecting how safe your assets may be across the crypto ecosystem.
- Bankless team
🙏 Thanks to our sponsor ACROSS
👉 Across.to is the bridge you deserve!
Your Crypto Is Not As Safe As You Think
Bankless Writer: Donovan Choy

Is your crypto safe? It’s probably not as safe as you think it is.
ETH on mainnet is not ETH on a rollup chain is not ETH bridged to an alt-L1 chain and is certainly not ETH held on a CEX.
The more a token is moved from its origin chain, the more security risks are stacked on your crypto holdings. Before you know it, your crypto is involved in an exploit and you’re staring glazy eyed at the Rekt Leaderboards wondering what you could’ve done differently.
Assessing your token security depends broadly on two criterion: the network security of the blockchain, and your personal wallet security.
- Blockchain network security: what is the security of the network that the token is currently held on? Is the validator set of that chain sufficiently decentralized? Is it vulnerable to a multisig exploit?
- Wallet security: how is the token secured on the wallet layer? Is it held in a centralized exchange, in your own MetaMask wallet or a multisig safe?
Consider the following scenarios:
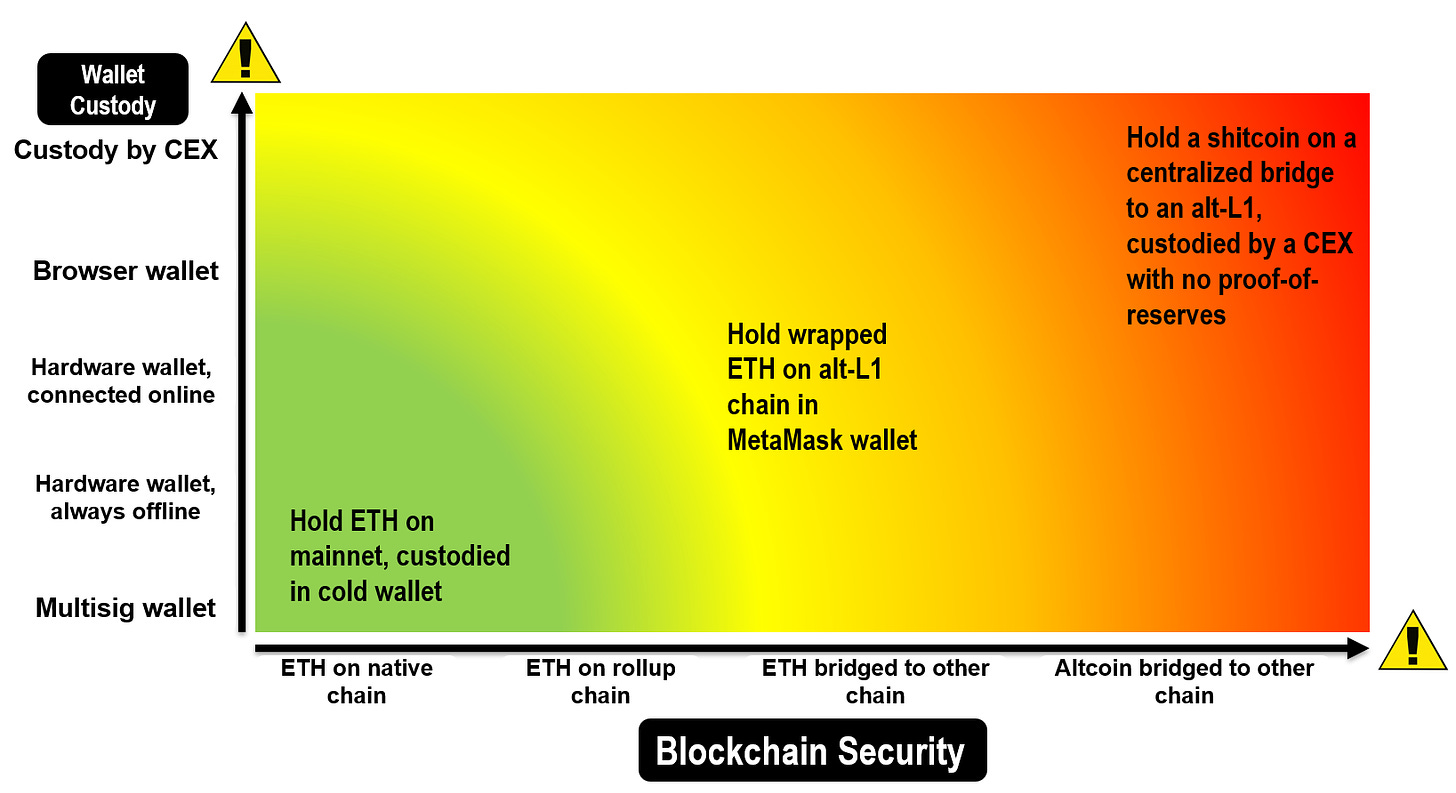
Scenario #1: Holding ETH on Ethereum mainnet 🌐
Abe is a finance major in his final year of college and has decided that stocks are for boomers. He takes his first step and buys ETH. Abe’s foray into crypto starts out pretty safely for the most part. His ETH is on Ethereum mainnet and it depends solely on the security of the origin chain itself. This is as safe as it gets.
As a general rule of thumb, the more decentralized a chain is, the less vulnerable it is to a 51% collusion attack as nodes are highly distributed. Ethereum is a highly decentralized chain with 4655 consensus nodes (514,000 validators), so Abe doesn’t need to worry. ETH also has a high market capitalization, which makes it extraordinarily expensive for a potential attacker to acquire 51% of all tokens to commit a network attack.
Scenario #2: Holding ETH on a rollup chain 🔗
Abe is now holding a sizable amount of ETH and rapidly descending down the crypto rabbithole. Ethereum mainnet is getting too slow for his needs (because it’s decentralized!), and he’s started taking baby steps into the world of Layer-2 rollup chains.
Rollup chains seemingly get to have their cake and eat it too. They’re faster than mainnet yet inherit Ethereum’s hardened security in contrast to L1 chains which are responsible for designing their own consensus security models.
Little does Abe know though that rollup infrastructure in practice today is still fairly centralized with several trust assumptions. Both Arbitrum and Optimism make use of centralized sequencers, the software entity that builds rollup blocks and submits transactions back down to Ethereum mainnet. While sequencers cannot post fraudulent transactions or steal money, it is capable of MEV-type sandwich attacks and transaction reordering to extract value. Ideally, rollups would allow multiple sequencers so users do not have to trust one sequencer to commit to a first-in-first-out policy for transactions.
Moreover, the fraud proof system of most Optimistic rollups – Optimism, Boba, Metis – are still under development and not live. Fraud proofs are Optimistic rollup’s “innocent until proven guilty” mechanism that let validators flag potentially fraudulent transactions before they get “rolled up” back to the Ethereum L1. At present, users are fully trusting one centralized block proposer to submit valid L1 state roots (Optimism has stated that decentralized sequencers and fraud proofs are coming mid-2023).
Arbitrum fairs slightly better than its competitors. While its fraud proof system is live, validators still need to be whitelisted, and are therefore not fully permissionless yet.
Finally, the smart contracts of most rollup chains are governed by a multi-signature (multisig) wallet. This means that funds locked in smart contracts can be withdrawn, or its contracts changed, if enough signatories in that wallet approve it.
Multisig security is undoubtedly better than a sole private key. It’s also an intended design and common for many new protocols in their early stages that want to retain the flexibility of upgrading their staking contracts for the future. Unfortunately, multisig risks are far from ideal. Case in point: The $625M Ronin bridge hack and Harmony bridge’s $100M hack both stemmed from multisig exploits.
Abe is worried, but multisig risk is fundamentally a black box and hard to quantify. There is no way to verify that multisig keys are safely maintained. To be fair, projects themselves may not want to reveal too much information to potential attackers either. How are the multisig keys kept? Are they in a password-protected spreadsheet? Who has access to that password? Are multisig keys individually distributed, or are all keys really controlled by the same person?
In sum, rollups in their full iteration will be decentralized, but still exist in a fairly centralized state with many trust assumptions today.
Scenario #3: Holding ETH bridged to a different blockchain 🌉
By now, Abe is too far beyond the point of no return in his burgeoning crypto “career”. He’s still an ETH-maxi at heart, but the juicy yields on alt-L1 chains like Solana and BNB Chain are too hard to ignore. He’s started bridging his ETH over to other chains using a cross-chain bridge. In doing so, he has inadvertently magnified the security risks of his ETH. His ETH now also depends on the security of the bridge and destination chain.
Abe’s ETH, once-ultrasound-money, is becoming less and less sound. Let’s consider the risks of bridges first, then the risk of altchains in turn.
Cross-chain bridges
Bridges all try to do the same thing but their protocol designs are different, and their security risks differ.
The most common types of bridges use lock and mint setups. These bridges are considered the least secure because they involve a centralized bridge operator locking up your deposited funds on one side of the bridge, then issuing you a wrapped synthetic asset on the other side, in effect an IOU of sorts. Their centralized nature makes them highly scalable but the least trustless as users have to hope that locked up reserves are always fully backed. Popular examples include Polygon’s PoS bridge, Binance’s Bridge or the WBTC bridge by Bitgo, Ren and Kyber Network.
The second type of bridges are liquidity network bridges. As its name suggests, they use liquidity pools. These bridges maintain liquidity pools on multiple chains that they use to “bridge” assets, similar to how FinTech companies like Wise or Revolut facilitate “transfers” across borders by maintaining bank accounts in different countries. By doing so, users receive the actual asset on the destination chain they’re bridging to, rather than a synthetic asset. Popular examples are Multichain, Portal, Stargate, Synapse, Hop and Across.
With both kinds of bridges, users incur a whole host of security risks. Here are some examples of security risks that exist on cross-chain bridges:
- Multichain uses multisigs to custody and transfer funds. Is that multisig secure? Multichain also runs on its own Multichain network which has 21 nodes. Is that validator setup sufficiently decentralized?
- Stargate bridge (built on LayerZero protocol) uses a sole, off-chain relayer to facilitate transfers. When will it be a decentralized relayer network?
- Bridges like Synapse V2 and Connext use optimistic fraud proofs. Are fraud proofs live?
- Wormhole bridge uses a set of distributed “guardian” nodes to observe on-chain messages and sign payloads, then combine signatures with other guardians to validate transactions. Recall that these “guardians” were bypassed in Wormhole’s February 2022 hack, so is the protection that these set of nodes offer sufficient?
- Across or LayerZero rely on third-party oracles. How is the oracle network governed in turn? Are they secure?
Terraform Labs will terminate the Terra Shuttle Bridge on Jan. 31.
— Windfall (@Windfall_Crypto) January 18, 2023
It is all good except that... Shuttle is 𝗶𝗻𝘀𝗼𝗹𝘃𝗲𝗻𝘁, 120 million $USTC 𝗮𝗿𝗲 𝗺𝗶𝘀𝘀𝗶𝗻𝗴, and TFL might 𝗺𝗶𝘀𝗮𝗽𝗽𝗿𝗼𝗽𝗿𝗶𝗮𝘁𝗲 the US$ 80M still held in the bridge.
A 🧵
1/10$LUNA $LUNC $MIR
The gold standard in trust-minimized bridging are light client bridges like Cosmos IBC and RainbowBridge. Light clients independently verify the consensus of the other chain for themselves, rather than trusting some third-party custodian (lock & mint bridges), a set of distributed nodes (Wormhole), validators on a sidechain (Synapse, cBridge), or a third-party oracle (LayerZero). Light clients are the most computationally intensive and hard to scale because every validator needs to run their own light client for each chain, but it means there is zero need to trust the bridge, and the only trust factor is the security of the other chain.
With all bridges: is the code of the bridge audited!? If in doubt, check the individual bridge pages of L2Beat.com. But still, proceed with caution. Even audited bridges like Poly Network and BNB Bridge have succumbed to half billion dollar exploits from bad code. In truth, no one can realistically assess the code of every protocol before they use it. The moral of the story is: when you use bridges, you need to know what you’re signing up for.
🚥 Alt-L1 chains
You’ve assessed the security of the bridge, the next question is: is the destination chain safe?
Solana
Solana’s validator set is fairly decentralized at ~2,124 consensus nodes. However, that does not mean that every node is controlled by an independent entity. If one entity ran multiple nodes, that would still be a worrying centralization risk, as that entity could shut off all its nodes. According to the Solana foundation, the number of independent entities running Solana nodes is 88.14%.
Cosmos
“Cosmos” is not a blockchain, but a network of many blockchains that run on common interoperability standards. As mentioned earlier, Cosmos bridging is relatively safer thanks to its trust-minimized form of bridging using light clients. However, you still need to consider the destination chain’s security. The main de-facto chain – Cosmos Hub – has 175 validators while Osmosis has 150.
Polygon
Polygon is sometimes referred to as a “Layer-2”, but L2s do not have their own validator set – the Polygon chain has a fairly centralized 100 validator set. Aside from its relatively centralized validator set, Polygon's main risk stems from its 5 of 9 multisig governance over its staking contracts, with projects such as Curve, QuickSwap, Cometh and Horizon in the fold. This exposes assets on the Polygon chain to a security risk should these multisig keys be compromised. Polygon plans to remove this security risk down the road by transitioning from multisig to regular DAO governance (MATIC holders would vote democratically on changes), introducing timelocks (a delay before changes go into effect) and eventually removing the upgradability of smart contracts and the subsequent multisig risk as its code proves to be battle-tested.
BNB Chain
BNB Chain is an EVM-compatible sidechain with a grand total of… 29 validators. When two million BNB were stolen from the BNB Bridge in October 2022, Binance was able to quickly coordinate with validators and unilaterally halt the BNB Chain. Need we say more?
🙏 Together with ⚡️ACROSS⚡️
Across is the bridge you deserve: fast speeds, low fees, great support, no hacks, and we love our users. Try it once and you’ll understand why Across users love us back and have bridged $billions with it.
Yield farmers will also find attractive yields for providing bridge liquidity! 👀

👉 If you have questions, check Twitter or the Discord!
Scenario #4: What if my token isn’t ETH? 👨🏼💻
Abe has thus far only bought and bridged a censorship-resistant crypto like ETH. But he has fully evolved into a full-blown crypto degen with an insatiable risk appetite. He’s turned his attention to… altcoins and NFTs.
Risks go up exponentially with altcoins because a new risk vector is introduced: the security of that DeFi protocol. Consider:
- Is the DeFi protocol a DEX or a lending market reliant on an oracle provider for its price feeds? How secure is the oracle?
- Are the protocol’s smart contracts or treasury governed by a multisig? How secure are they? Remember when the treasury manager of Wonderland protocol turned out to be a known scammer of a failed exchange?
- Regarding DAO governance, how distributed is the token – are they concentrated in the hands of whales? Historically, DAOs like Beanstalk and Mango Markets have been caught up in governance attacks where the hackers were able to acquire huge amounts of voting power.
You are much more likely to be rugged by a DeFi protocol than an L1 blockchain considering the ease of creating a dapp (writing code on-chain), as opposed to bootstrapping the security of an entire blockchain.
Finally, perhaps worse than altcoins are fully centralized tokens like XRP, USDC, USDT and BUSD that are issued by centralized institutions and can be subject to political pressure, as shown by the SEC’s threat to sue BUSD issuer Paxos just last week.
💸 Wallet security
We’ve looked at blockchain security, now we turn to wallet security. The best protocol security designs in the world won’t matter if you don't keep your front door locked. Beginning with the highest risk…
5️. You’re holding your crypto in a CEX or lender.
This is the highest risk and least trustless form of costody. You’re fully trusting a centralized institution not to pull a Sam Bankman-Fried. This is a major red flag. 🚩 If you have to trust a CEX with your crypto, perhaps for on/off-ramping, make sure it has verified and regularly updated proof-of-reserves (see Nansen). This is an improvement, but still fairly high risk. The company might truthfully hold lots of reserves, but you don’t know anything about their debt/liabilities.
4️. Hold crypto in a “hot” browser wallet like MetaMask.
Congrats, you’re a full custodian of your own crypto now. This was the whole point, remember? However, hot wallets are considered less secure than a cold, hardware wallet because your private keys are generated and exposed online. From the hacks of Wintermute and Bitmart and Vulcan Forged to so many Bored Ape holders, there is no shortage of examples of hot wallet private keys being compromised.
3️. Hold crypto in a “cold” hardware wallet like Ledger, then connect it to MetaMask to easily navigate DeFi.
This ensures that your seed phrase is generated offline on your Ledger. Every transaction you execute on MetaMask needs to be confirmed on your hardware wallet. The remaining security risk here is exposure to signing malicious contracts online. Only a level 99 tech wizard can protect you from this, although there are some interesting applications like Blowfish tackling this problem.
2️. Hold crypto exclusively in your own hardware wallet that is never connected online.
This is the gold standard of crypto custodianship. Write your private keys down, or store it on a steel capsule if you’re worried about WW3.
1️. Hold crypto in a multisig wallet with several trusted parties.
The easiest way to set up a multisig wallet is with “Gnosis Safes”. Just make sure you don’t pick someone like a partner you plan to divorce.
🔐 Takeaways
Transacting in crypto regularly means making tradeoffs on a daily basis. This article is not meant to be an indictment or attack on these protocols or products but a guide to assessing the security of your crypto.
TLDR: Crypto is safest when you hold your tokens on the native chain. The worst security holding is a shitcoin bridged to a centralized chain with weak security, custodied by a sketchy CEX. If you’re doing this, I pray you sleep well at night.