🏴 How to Prevent Crypto Wallet Hacks


Earlier this month, we released a brand new set of updates to our Token Ratings. Haven’t read through yet? Here’s what you’re missing out on:
- The team’s verdict on SAND, INDEX, and FXS 📈
- Which tokens are going to be affected by upcoming insider token unlocks 🔒
- How we think the Shanghai Upgrade will impact token price 📊
- And much more.
As always, the first token is available to everyone, but you’ll need to upgrade to Bankless Premium to get access to the rest.
Dear Bankless Nation,
Last week, Moonbirds creator Kevin Rose fell prey to a phishing attack that led to his wallet getting hacked for ~684 ETH worth of NFTs.
If it can happen to a Web3 guru, it can happen to you too. Peep our wallet security best practices and bring your crypto assets under security lockdown today.
- Bankless team
🙏 Together with ⚡️KRAKEN⚡️
Kraken, the secure, transparent, reliable digital asset exchange, makes it easy to instantly buy 200+ cryptocurrencies with fast, flexible funding options. Your account is covered with industry-leading security and award-winning Client Engagement, available 24/7.
👉 Visit Kraken.com to learn more and start your experience today.
How to Prevent Crypto Wallet Hacks
Bankless Writer: William M. Peaster, Bankless contributor and Metaversal writer

Crypto wallet hacks have already led to millions of dollars’ worth of digital asset thefts in 2023.
This Bankless tactic will show you how to use a layered, multi-faceted approach to resolutely defend your wallets from getting drained of their crypto and NFTs.
- Goal: Learn how to set up a defensive wallet system
- Skill: Intermediate to Advanced
- Effort: A couple hours
- ROI: Peace of mind knowing your assets are protected
A strategic defense for protecting your crypto

To sign or not to sign: the basic dangers of crypto wallets
“Hot” crypto wallets are online software wallets, namely browser extensions like MetaMask and mobile apps like Rainbow.
These sorts of wallets are particularly popular because of their ease of use. The catch, though? A hacker can readily drain wallets if they compromise your account password or seed phrase.
This is where “cold” crypto wallets come in. From paper wallets to hardware wallets, these methods ensure the private keys of your addresses are forever firewalled from the internet, thus mitigating many hack vectors.
Here, note that MetaMask and other hot wallets are just interfaces. You can link your cold hardware wallet, like a Ledger, to use through these popular interfaces and get the best of both worlds: slick UX and solid security.
However, resources like hardware wallets aren’t a catch-all solution for defending your crypto and NFTs. The underlying security these devices provide is only as good as the transactions you sign.
In light of recent events, I've been seeing a lot of questions regarding what is and isn't safe to sign, as well as a lot of misinformed answers.
— quit.q00t.eth (@0xQuit) January 27, 2023
It's important that we aim to understand signatures, not avoid them. They're a key component of a decentralized web3.
1/🧵
In other words, if you get tricked into signing a nefarious transaction crafted by a hacker, they can abuse any active token approvals you have in order to drain all approved tokens you have from your wallet.
A crypto insider gets hit with a malicious signature
Last week, the crypto space was reminded just how biting this attack vector can be when Kevin Rose, the co-founder of projects like Proof Collective and Moonbirds, saw one of his wallets drained of dozens of NFT grails upon signing a seemingly legit, but actually malicious, transaction.
It looks like @kevinrose wallet was just compromised...
— Cirrus (@CirrusNFT) January 25, 2023
Millions and millions in NFTs drained... pic.twitter.com/GjK2gdHbmU
It’s sadly all too understandable — we’ve seen plenty of these types of thefts before. Rose thought he was minting from a real Memes Collection by 6529 drop, but it was actually a trap website that prompted a signature for a fake mint. The signature request looked unintelligible to the human eye, similar to this:
It's amazing how many crypto bros see this and still blame the user... pic.twitter.com/jrEiUSGEDy
— 6457.eth (@JKrantz) January 26, 2023
In reality, though, the signature Rose signed was for a poisonous specially-crafted OpenSea sales bundle transaction that targeted all the NFTs he had active approvals for, thus sweeping them to the attacker essentially for free.
Mind you, in the DeFi and the NFT ecosystems it’s common to conduct approval transactions for tokens you’re trading. This lets a smart contract access your tokens.
If you give OpenSea unlimited approval to spend your Bored Apes, for example, this then lets you list any of the BAYC NFTs you hold on OpenSea’s SeaPort protocol. A hacker can do the same if they commandeer your wallet, however!
As such, the hack of Kevin Rose’s wallet capitalized on the cumulative effect of three factors:
- The fake mint site being convincing enough
- The theft transaction actually being signed
- Valuable token approvals being available to take advantage of
The L.A.S.H. Defense 101
The good news? There is a specific series of security resources that, when properly used in tandem, can resolutely shield your wallets from getting drained. I call these resources and their complementary applications together the L.A.S.H. (Layered Software and Hardware) system for crypto security.
- 📱 Start with hardware wallets — Use cold wallets like Ledger devices, which shield private keys from ever touching the internet, to underpin and interface with your main casual crypto accounts
- 💎 Consolidate with a vault — Create a digital vault for your most valuable crypto and NFTs via advanced account solutions like Safe (for creating multi-signature wallets) and/or Argent (for creating smart contract wallets with social recovery guardians)
- 🔏 Double down with security apps — Rely on security apps like delegate.cash (for firewalling important cold wallets), Stelo (for human-readable transaction warnings), and revoke.cash (for cleaning your token allowances) to defend your wallet network
Hardware wallets as base command

Ledgers, Trezors, GridPlus Lattices, oh my! The choice is yours, but you’ve got to choose.
You want to keep your digital eggs in different baskets, so to speak, so let’s say you want to have three different casual wallets: one for general DeFi activities, one for minting your own NFTs, and one for collecting other people’s NFTs.
Good idea, but consider using a separate hardware wallet to underpin each of these addresses! That way a hacker can’t scrape any of your casual accounts even if, say, they compromised the password to your MetaMask extension.
Here, though, there are a couple important things to keep in mind:
- Only purchase hardware wallets directly from manufacturers’ websites — you don’t want to face the chance, however unlikely, that your device was tinkered with at a third-party retailer
- Safely secure your seed phrases — whether you use a fireproof safe, multiple bank deposit boxes via Shamir’s secret sharing, or stenography + a tattoo (it’s possible!), take your seed phrase storage seriously because these are like “god mode” passwords for your associated addresses
Set up a vault for your best assets
Once you have your casual wallets taken care of, it’s time to prepare a digital vault.
In the colloquial sense, a vault is a wallet you designate for long-term storage of your crypto and NFTs. You isolate it from casual activities, like minting from new drops, to sidestep active token approvals and transaction signature attacks.
imagine there was such a thing as a $1 Million Dollar Bill, and you had one
— DCinvestor.eth ⌐◨-◨ (@iamDCinvestor) January 25, 2023
would you keep it in the wallet you used to go to the grocery store with?
probably not. could be stolen, you might use it to pay by accident, etc.
yet we do this sort of thing in crypto all of the time
The idea, then, is to transfer your most valuable assets into your vault and then just let them sit there for safekeeping. If the time comes that you need to sell anything from your vault, e.g. an NFT with a mooning floor, transfer it to a separate wallet first so your vault never has to carry active token approvals. This way, it’ll be firewalled from threats.
Yet what’s the best way to go about making a vault?
Of course, a “vault” is just a status designation. You can use a spare hardware wallet you have as a vault, for instance. But I recommend going above and beyond with solutions that can protect your crypto and NFTs through multiple layers of security, like a Safe multi-signature wallet or an Argent smart contract wallet.
With Safe, you can set up a vault using three different hardware wallets for a 2-of-3 multisig, or five wallets for a 3-of-5 multisig, etc. In a 2-of-3, for example, it’d take any combo of two signatures from your three designated wallets to confirm any transaction from your vault.
These additional layers of transaction redundancy are powerful because thanks to them an attacker no longer needs to compromise just one address to steal your grails but instead multiple addresses, which is improbable. And fortunately, it’s straightforward to use Safe. You would:
- Go to app.safe.global/welcome, connect a wallet, and press the Create new safe button
- Select your deployment chain — Ethereum and 10 other networks are currently supported
- Name your safe, e.g. “My Vault”
- Input the other addresses you want to configure your multisig with
- Press the Create button, then complete the deployment transaction, and voila!
As for Argent, it’s a smart wallet system. This means when you create a wallet through Argent, it’s actually a smart contract on Ethereum rather than just a simple address. This design is very compelling, as it allows you to eschew dealing with private keys, to socially recover your account and to avoid untrusted transactions through Guardians.
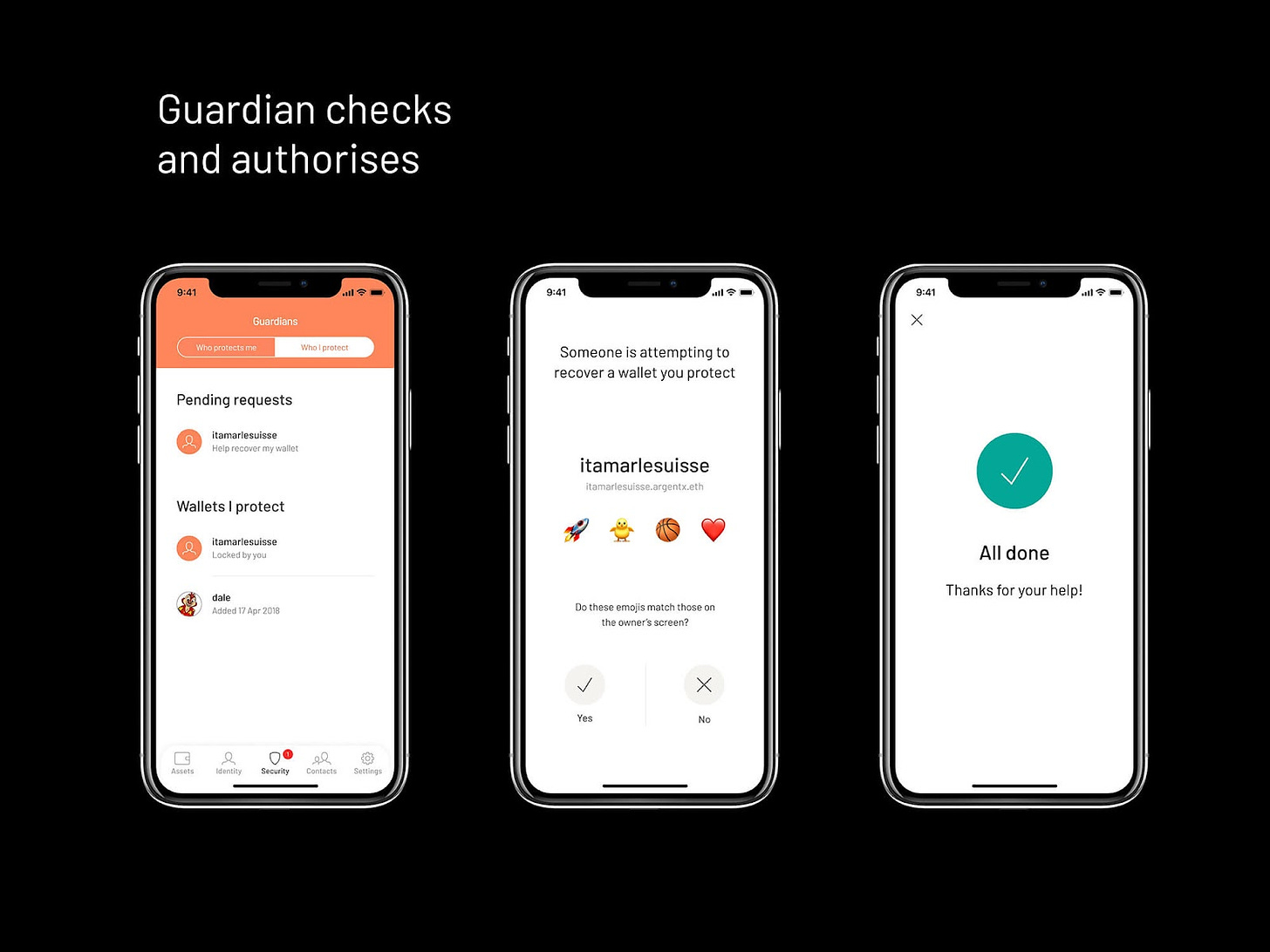
Simply put, a Guardian is a trusted third party that you designate to help you maintain control of your wallet. You can select family members or close friends or even extra hardware wallets you control. In Argent you designate which addresses you trust, and then interacting with any addresses not on that list will require approval from Guardians.
These layered recovery and trust mechanisms make Argent another interesting option for your digital vault. To create an Argent wallet you’d:
- Download the Argent Android or iOS app
- Open the app and press Create new wallet when prompted
- Reserve a username and then read and accept the terms of service
- Enter your email address and phone number, then verify your email and supply the verification code texted to your phone
- Choose a passcode to protect your wallet and activate your Ethereum account, and that’s it!
Level up your defenses with security apps
Lastly, in the L.A.S.H. system you want to complement your base wallets and vault with some of the really helpful crypto security apps that are currently available. Top of mind examples include:
- 🤲 delegate.cash — Has your vault been allowlisted for a hot new NFT mint, but you don’t want to mint from there? Services like delegate.cash let you delegate your cold wallet’s powers to a hot wallet of your choice so your underlying assets stay siloed at all times
- ❌ revoke.cash — Connect your wallet to revoke.cash to review and remove token allowances you’re not using any more as part of your regular crypto security routine… rug the attackers before they can rug you!
- 🛡️ Stelo — This is a browser extension you can download that will turn your unintelligible wallet signature requests into human-readable messages or, if needed, human-readable warnings; this can become your first line of defense for avoiding bad transactions
11/ We reverse-engineered the signature that @kevinrose signed and passed it through Stelo.
— Stelo - Keep your crypto safe (@stelolabs) January 26, 2023
If @kevinrose had Stelo this is what he would have seen: pic.twitter.com/VODKWV71IO
Zooming out
The L.A.S.H. approach to crypto security offers layers of defense for both your casual and vault wallets. When you combine the assurances provided by hardware wallets, multisigs, account delegation, routine token approval cleanings, and human-readable signatures, you get a security system that is redundant in its protections and has no single point of failure.
If you’re looking to batten down your crypto security for good, I recommend using this gamut of solutions in tandem for practical and effective safety!
Action steps
- Double down on your crypto security: Use hardware wallets, a digital vault, and crypto security apps like Stelo 🛡️
- Read my previous tactic if you missed it: How to Use Decentralized Stablecoins 🪙
Author Bio
William M. Peaster is a professional writer and creator of Metaversal — a new Bankless newsletter focused on the emergence of NFTs in the cryptoeconomy. He’s also recently been contributing content to Bankless, JPG, and beyond!
Subscribe to Bankless. $22 per mo. Includes archive access, Inner Circle & Badge.
🙏 Thanks to our sponsor KRAKEN
👉 Kraken has been on the forefront of the blockchain revolution since 2011 ✨
