Dear Bankless Nation,
Bear market builders won't stop, but making all of the latest blockchain networks play nice with each other isn't so easy.
In today's newsletter, we dissect the risks and latest innovations in cross-chain bridges – a high-value target for hackers with nearly $2.7 billion stolen from them to date!
-Bankless team
Guest Writer: Paul Timofeev
Last month, amid all of the excitement around institutional crypto support and regulatory wins, DeFi was reminded once again of one of its greatest vulnerabilities – cross-chain security.
Or lack there of...
1. On May 21, 2023, Multichain CEO Zhaojun was taken away by the Chinese police from his home and has been out of contact with the global Multichain team ever since. The team contacted the MPC node operators and learned that their operational access keys to MPC node servers had…
— Multichain (Previously Anyswap) (@MultichainOrg) July 14, 2023
The Multichain Bridge, which at one point boasted over $10 billion in TVL, experienced a mysterious exploit in which $130 million of user funds were drained and lost. The incident pushed the TVH (Total Value Hacked) on bridges to a whopping $2.66 billion USD!
This frighteningly large number of hacked funds begs the question – why are bridges still so vulnerable? To understand, let's quickly revisit the fundamentals of what bridges are and how they work.
Bridges TL;DR
A bridge is most simply a connector between point A and point B. Blockchain bridges are no different – they enable a sender on chain A to easily communicate with a receiver on chain B.
These bridges emerged to meet the need for interoperability between different chains in a growing multi-chain world. By default, blockchains are like stranded islands with no native mechanisms for external communication.
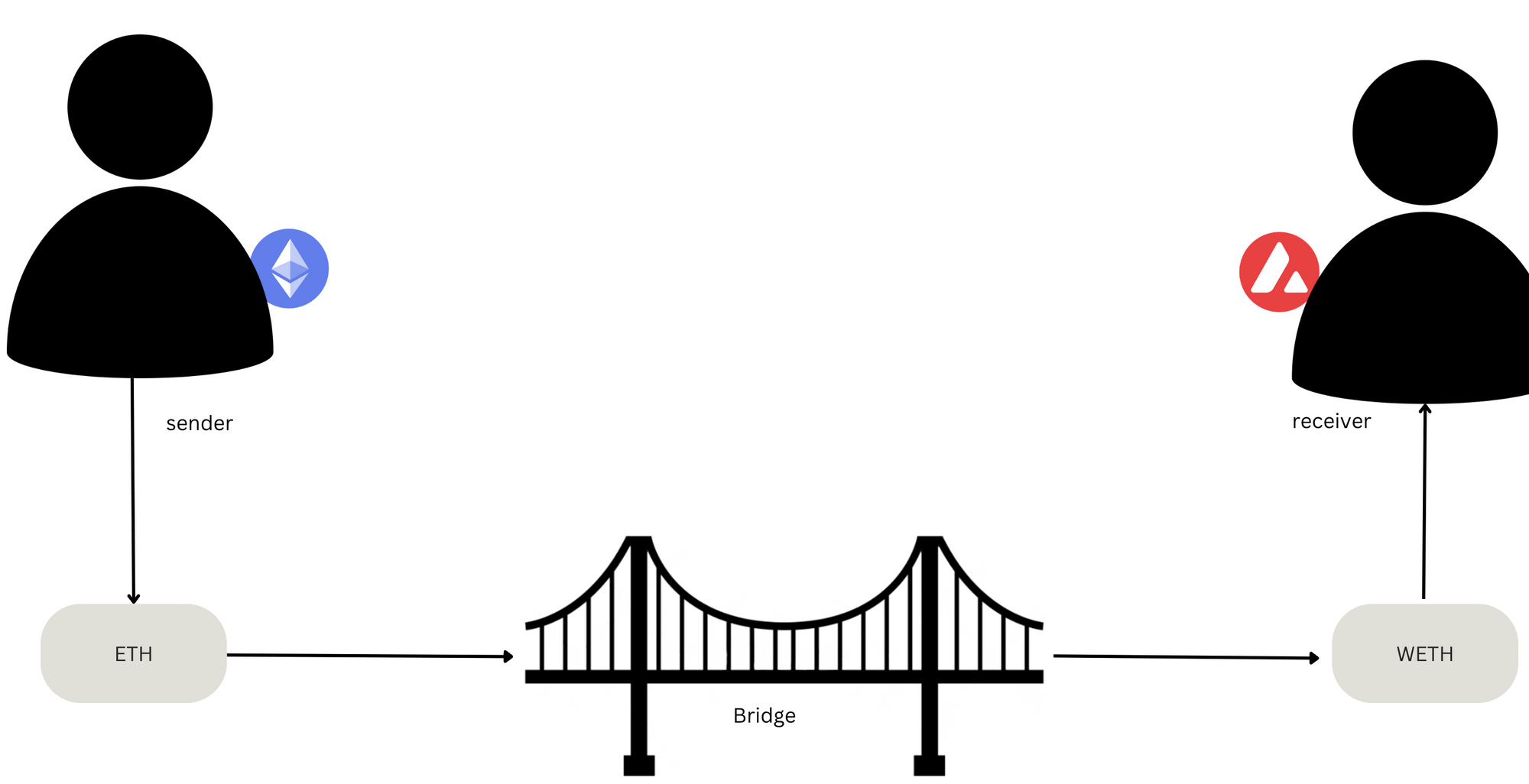
Bridges solved this by building the necessary pathways for communication, enabling users to transfer assets and value across chains without needing to deploy additional capital onchain. They also enabled application developers to build and implement various cross-chain functions such as cross-chain borrow/lending, cross-chain governance, and more.
Cross-chain interoperability set the stage for a new suite of applications and onchain utilities in crypto.
Inherent Security Trade-offs
Blockchains rely on a set of entities known as validators to verify and execute transactions. When a user submits their transaction to be executed, they are trusting the validators to act honestly and complete the transaction.
Bridges operate the same way – they rely on validators to verify and process cross-chain transactions. In fact, many (though not all) bridges introduce additional layers of trust and security, and therefore risk.
Now, below let's dig into the most common verification systems that bridges use today so we can track the advantages and shortcomings that each hold.
BUT before we do, let's frame the conversation with the central question anyone using a bridge should be asking: 👇👇👇
Who is verifying the system and how much does it cost to corrupt them? - Connext's Arjun Bhuptani
So, how Are Bridges Verified? 👷♂️
Different bridges use different mechanisms to facilitate cross-chain communication – the key distinction is which set of validators is responsible for verifying the transactions and other data being exchanged.
Generally, bridges are either externally, natively, or locally verified.
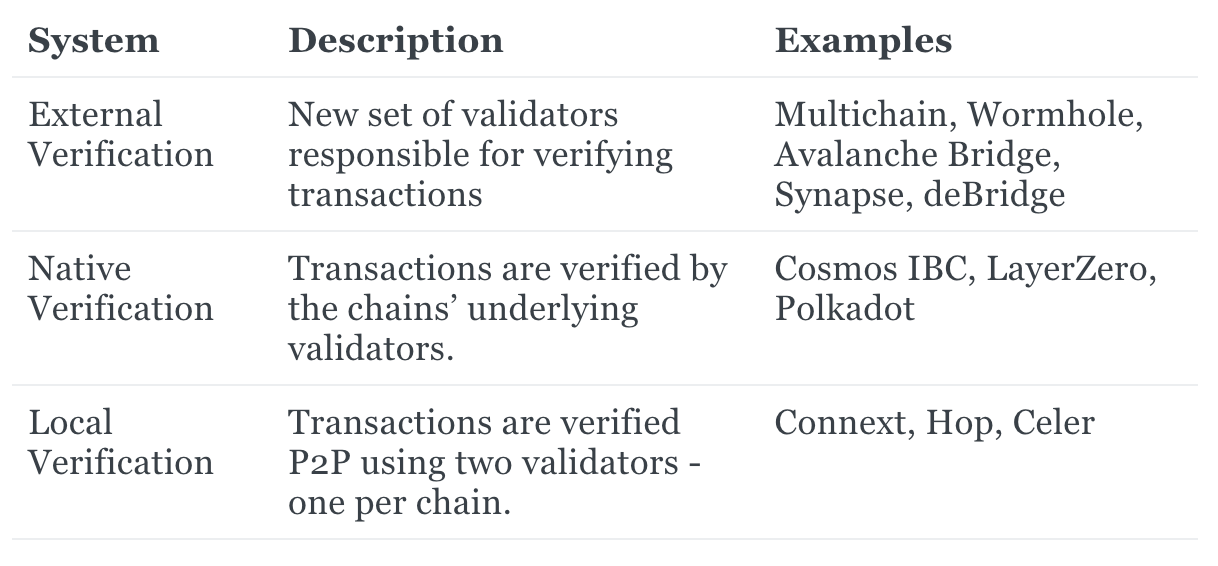
◼️ External Verification
Externally verified bridges introduce an external set of validators responsible for verifying transaction data traveling across chains. Anyone who uses these bridges is taking on additional risk as this new validator set brings its own unique trust assumptions in addition to the source and destination chains.
These bridges usually adopt the lock-and-mint model – locking a user's native assets in a wallet on the source chain, and minting the equivalent amount in "wrapped" assets on the destination chain. Those wallets are controlled and operated by the external validators, and so is the bridge itself.
While these types of bridges often optimize for speed and connectivity, they are prone to attacks as the wallets which store user assets become lucrative targets for hackers.
A few events/entities of note:
- The Ronin Bridge got hacked for $625M after a hacker was able to gain control over the majority of validators for a multi-sig wallet – a classic case of compromised private keys!
- Multichain implemented its own Multi-Party Computation (MPC) network of validators for verifying and signing transactions. The bridge experienced $130M of allegedly unauthorized withdrawals, promptly followed by the arrest of the CEO. While it is yet to be confirmed whether this was an external hack or an insider rug pull, the arrest compromised the platform’s MPC keys, forcing the team to shut down the bridge indefinitely.
- Thorchain is an app-specific chain which also serves as a cross-chain DEX. This means in addition to trusting the validators on the source and destination chains, users must also trust the validators on this intermediary chain. Although validators must stake collateral which can be slashed in order to participate, this mechanism is still not guaranteed to be more secure as Thorchain had been hacked previously for $8 million.
◼️ Native Verification
Natively verified bridges rely solely on the validators of the underlying chains for verifying cross-chain transactions. They do not introduce a new set of validators, and therefore do not create an additional layer of trust and risk.
These bridges often use Light clients and Relay systems. Validators are responsible for generating “proofs” about the transaction data coming from the source chain. These proofs are then transmitted, or relayed, to smart contracts known as Light clients, which verify the contents of the proof, and alert validators on the destination chain to complete the transaction.
While these systems are generally more secure than externally verified bridges, they are often resource-intensive as teams need to build smart contracts on each new destination chain. Additionally, the entire process is done onchain, which incurs high costs for paying gas fees.
The Cosmos Inter-Blockchain Communication (IBC) protocol is a classic example of a natively verified bridge. Using a light client to verify cross-chain messages, IBC enables Cosmos chains to communicate with one another seamlessly.
◼️ Local Verification
Similar to natively verified bridges, locally verified systems do not introduce any new validator sets to our cross-chain equation. In fact, they only require two validators, one from each chain, as opposed to the entire validator sets.
These validators are responsible for exchanging proofs for their own corresponding chain – if both proofs are valid, then the validators can exchange assets and complete the transaction process.
Note this model is limited to asset transfers, and does not allow for generalized message passing, which is what enables more complex cross-chain functionality such as borrow/lending, governance, yield farming, etc. In addition, the exchange of proofs can result in slower performance.
One example of this type of bridge design is Connext. Users can provide liquidity on supported chains for the bridge, and a set of smart contracts and off-chain agents facilitate the exchange of assets using said liquidity pools.

Building Secure Cross-Chain Solutions 🔐
Cross-chain protocols continue to remain a topic of controversy in the crypto community as bridges remain a susceptible target to exploits – to the extent that some believe a fragmented multi-chain world still outweighs the security risks of cross-chain interoperability.
For instance, Vitalik Buterin has previously explained why he is not so optimistic on cross-chain protocols:
...there really are a few separate communities with different values and it's better for them to live separately than all fight over influence on the same thing… cross-chain activity has an anti-network-effect: while there's not much of it going on, it's pretty safe, but the more of it is happening, the more the risks go up.
On the other hand, some others believe uniting the fragmented multi-chain world is key to mass adoption and value capture for blockchains, and that cross-chain interoperability will enable this.
Just like key standards such as TCP/IP remade a fragmented early internet into the single global internet we all know and use today, we are making CCIP to connect the fragmented public blockchain landscape and the growing bank chain ecosystem into a single Internet of Contracts.… https://t.co/BDMFMfknY2 pic.twitter.com/DDscglD2An
— Sergey Nazarov (@SergeyNazarov) July 17, 2023
Important To Get Right!
Wherever you stand on interoperability, it's clear we're looking at a multi-chain future in some sense.
We have witnessed the rise (and fall) of many L1s over the past couple years. These days, rollups are the talk of the town and primed for growth, with EIP-4844 set to bring lower fees and greater throughput for many rollups, and protocols like Celestia paving the path for a world of modular rollups.
Whether users are wanting to borrow/lend/farm across chains, DAOs are looking to participate in cross-chain governance, or enterprises are wishing to connect their private chains with a public chain, the demand for cross-chain infrastructure will continue to grow.
Enforcing stricter security measures will be an important part of developing secure cross-chain communication, and the infrastructure to support this function will be critical for the future of blockchains!
